

Digitalization, digital networking, research, network automation, education and educational networks; are all these the buzz words of recent technology and for education institutions? Why everyone is talking about digitalization and networks, how are these both interconnected; and what is network automation and education networks are what we are going to know on this blog today .
While what the smaller research say about the education networks and individual campus networks; we can say that both stand for the same aim which is implementing education through current network automation strategies and tools. Are these tools, strategies, and significant efficiencies or the network automation wave more hype than these smaller institutions?
Let us look at some of the regional networks, how they are succeeded and what are the challenges involved in this path of deploying various network automation with relatively small and outsourced staff and support. Also discussed will be the experience of working with this diverse technology and how it increased the awareness about the possible proposed value of network automation and how regional’s can assist smaller schools through this network path.
Digital learning and collaboration have become an essential part of today’s education. From k-12 schools are implementing the methods of digital learning. These blended learning methods and one to one computing programs are reshaping the classroom studies and engaging more students to become tech-savvy’s. The higher educational institutions are announcing BYOD- which means bring your own device concept; students are also allowed to use their smart phones, laptops, tablets and other gadgets to be connected. This helps the institutions to meet the unprecedented demand for connectivity with high performance and to get recognized as highly reliable campus and data network center solution provider.
Challenges:
The hike of latest technologies, mobile devices and growing appetite for applications and rising security concerns are placing new burdens on educational networks. To meet these challenges, schools are expanding their networks to meet student and faculty expectations for high performance, highly reliable, and always-on connectivity.
The school network is always mission-critical, and downtime will be more and un-tolerable when class lectures, research projects, assignments are involved. We can see diversity and richness using these educational applications as learning is increasingly leveraging interactive curricula, collaboration tools, streaming media, and digital media. The success of the Common Core Assessments hugely depends on connectivity. The higher education, universities, and colleges that have poor quality, non-ubiquitous network access, quickly discover that this is affecting their registration/enrollment rates.
The other challenge is with the number of Wi-Fi devices and the types of devices students bring to a university or college campus; Students commonly have three or more devices like; smartphone, tablet, laptop, gaming device, or streaming media player and expect flawless connectivity. While higher education is deploying wireless IP phones for better communications, IP video cameras to develop physical security, and sensors for a more efficient environment. The projections for the Internet of Things, which will connect hundreds of billions of devices in a few short years, are nothing short of staggering.
The trends that educational networks are looking today for students, faculties and administrator expectations is that of for the connectivity which is rising and the complexity and cost of networking are also growing exponentially. In addition to this growth, the “adding on” to networking equipment for old designs is causing the network to become ever more fragile. IT budgets are tight, and technology necessities are growing faster than the funding.
What if schools took a step back and had a unique opportunity to proactively aim their networks to meet the challenges which hit today and tomorrow? What if deploying the network was simple, not a manual, time-consuming chore? What if your initial design and build could scale for years to come, without having to build configurations on the fly every time? What if networks were easier to plan and build, configure and deploy, visualize and monitor—and had automated troubleshooting and broad reporting?
The tools which are of high configurations help the educational networks are Juniper Networks, HP, CODE42, DLT, EKINOPS, Level 3, cloudyCluster, OSI and much more. It’s time to update the educational institutions towards the design, building, and maintaining the network and taking the advantage of automation and modern management tools to create scale, consistency, and efficiency.
...
Read More

Artificial intelligence has been spread over a very large area of computing since the beginning of the computer, but we are getting closer than ever with cognitive computing models. What are these models and why are we talking about it today.
Cognitive computing comes from a mash-up of cognitive science which is the study of the human brain and how it functions and a touch of computer science and the results will have far-reaching impacts on our private lives, healthcare, business, and more.
What is Cognitive Computing?
The aim of cognitive computing is to replicate human thought processes in a programmed model. It describes technology platforms that broadly speaking, and which are involved in self-learning systems that use data mining, natural language processing, and pattern recognition to mimic the way the human brain works. With the goal to automate the IT systems that are capable of solving the problems without requiring human assistance the Cognitive computing is growing very fast.
Cognitive computing systems use machine learning algorithms; which repeatedly acquire knowledge from the data fed into them by mining data for information. These systems treat the way they look for patterns and as well as the way they process data so they have become competent of anticipating new problems and modeling possible solutions.
Cognitive computing is used in numerous artificial intelligence applications (AI), including expert systems, neural networks, natural language programming, robotics and virtual reality. While computers are proved the faster machines at calculations and meting out the humans for decades; these machines haven’t been able to accomplish some tasks that humans take for granted as simple, like understanding natural language, or recognizing unique objects in an image. The cognitive computing represents the third era of computing: it from computers that could tabulate sums (the 1900s) to programmable systems (1950s), and now to cognitive systems.
The cognitive systems; most remarkably IBM and IBM +0.55%’s Watson, depend on deep learning algorithms and neural networks to process the information by comparing it to an education set of data. The more data the systems are exposed to, the more it learns, and the more accurate it becomes over time, and this type of neural network is a complex “tree” of decisions the computer can make to arrive at an answer.
What can cognitive computing do?
As per the recent TED Talk from IBM, Watson could ultimately be applied in a healthcare setting also, this helps the administrative department of healthcare to collate the span of knowledge around conditions, which include the patient history, journal articles, best practices, diagnostic tools, and many more. Through this, you can easily analyze that vast quantity of information, and provide your recommendations as needed.
The next stage is to examine, which will be proceeded by the consulting doctor, who will then be able to look at the evidence and based on the recorded evidence the treatment options will be released based on these large number of factors including the individual patient’s presentation and history. Hopefully, this will lead to making better treatment decisions.
While in other scenarios, when the goal is not to clear and you look to replace the doctor, and the doctor’s capabilities by processing the humongous amount of data available will not be retained by any human and thus providing a summary of potential application will be overdue. This type of process could be done for any field such as including finance, law, and education in which large quantities of complex data will be in need to be processed and analyzed to solve problems.
However, you can also apply these systems in other areas of business like consumer behavior analysis, personal shopping bots, travel agents, tutors, customer support bots, security, and diagnostics. We see that there are personal digital assistants available nowadays in our personal phones and computers like —Siri and Google GOOGL -0.21% among others, which are not true cognitive systems; and have a pre-programmed set of responses and can only respond to a preset number of requests. But, as tech is on high volume we will be able to address our phones, our computers, our cars, our smart houses and get a real time in the near future when thoughtful response rather than a pre-programmed one.
The coming future will be more delightful for us as computers will become more like humans and they will also expand our capabilities and knowledge. Just be ready to welcome the coming era when computers can enhance human knowledge and ingenuity in entirely new ways.
...
Read More

The Internet of Things (IoT) has quickly turned out to be one of the most adapted and maybe, most advertised jargons across IT & ITES industry. However, it is completely defensible and is backed up by the numbers. Beyond of its extensive range of benefits, the state of the art of this trend being involved in the IT sector is inevitable.
The IoT of things are not all-purpose devices, such as smartphones and computers, but dedicated objects, such as vending machines, jet engines, connected soap dispensers and many other countless examples.
IoT will have a great impact on the economy and many enterprises will look into transforming their businesses into digital and facilitate their business models by improving efficiency to generate good ROI. It’s a tradition that enterprises always look up for successful trends and for sure Industries are looking at IoT, but the implementation is still premature. Even though there is some immaturity, but there is still some evidence of planned uses across a wide range of industries. We may find an answer from these existing evidence to the question of the hour, what needs to be done to build IoT at the enterprise level.
Sensors
Objects that contain sensors found useful in all studies, for example, you can fix a sensor to the products in a grocery store and if the item is spoiled it will give you a buzz to replace the item, the cost of purchase and installation of a sensor is relatively cheap and it also reduce the stress on the workforce.
Connectivity
You can always stay connected to your IoT device via your smartphone or through a hub or the device itself contains the Internet connectivity.
Processors
Without a processor there is no computing or a smart device. IoT devices will have capabilities of computing and storing relevant data passed on to it. There is a need to equip these devices with some useful features, so there is a need of advanced processors equipped with these devices.
Energy-efficiency
Think about the high-end business models, where there will a lot of flow of customer and immense pressure on your workforce, you need a device which has the conservative amount of energy, which will not ask you for a battery charger or replacement battery during peak hours.
Cost Effectiveness
The Business goal of IT companies is providing the users with the technology and features that they needed the most. However, there will be a significant cost for maintaining and supporting the user’s technology. IoT is the answer to reducing the signification cost and ensure flawless deliverability in the IT process or project.
Quality Standards
You need to operate your devices under harsh outdoor atmospheric conditions for a long time. There should be proper parameters and quality checks on the (IoT) devices produced by the industries.
Security
Securing your device or network is a critical mission, Devices that are associated with a network through IP’s have immense threats of being hacked/spoofed. Managing ID’s and access, saving the databases are critical to the triumph of the IoT. However, traditional approach and old school techniques cannot cope with the complexity that the IoT needs from the enterprise. It is the time for Business leaders and technology giants to reconsider their approach towards cyber security, and they should raise the curtains for the new set of security rules.
...
Read More

Search has become integrated into the fabric of our society. With more than 197.9 billion searches performed worldwide each year since April 2014, more or less 6.6 billion web searches will be performed every day. That means on an average about 7,500 searches are performed every single second of a day. Moreover; users have grown to wait for that the responses to their search queries will be returned in less than one second.
If you have ever come across, the various “SEO is dead”, that claims to make the rounds play periodically in the digital marketing world, rest assured — SEO is both alive and well — and has not as many feared and been killed by social media marketing as a driver of web traffic. However, in November 2014, Twitter announced that by renewing its focus on SEO, it has increased the numbers of visitors coming to the site tenfold — from 7.5 million to 76 million visitors in a month.
The demand for search continues to be high; because of the people can now obtain in mere seconds information that 20 years ago would have required planning a trip to the nearest library, the usage of card catalog and the Dewey Decimal system and a physical search through halls of printed volumes — a process that could easily have consumed two hours or more. Through the new channel of search, people can now conduct many of their favorite searches, shopping, banking and personal transactions online—somewhat the things have changed the way our global population lives, interacts, and connects to each other.
The dramatic shift in behavior represents what the investors are likely to label a disruptive event – an event that has changed something in a fundamental way. Search Engines have been always the center of this disruptive event, and having businesses on website con-tent appears highly in the search engines when people try to look for the service, product or for any resource that business provides is critical to its survival. This is the situation for every business now and then; as most of the paths to success, obtaining such prime search results in real estate is not a simple matter. However, this is how the search engine optimization works in promoting your business.
The Mission of SEO

Web searches are free to use and yet very informative; as there are many available search engines to find what they are seeking, so the burden is on the search engines to develop a related, fast and fresh search experience. Most of the part search engines achieve this by being professed as having the most relevant results and delivering them the fastest, the users will search thinking that they will get them to what they are looking in for and want it in the least amount of time.
As a result, search engines invest an incredible amount of energy, time and capital in improving their significance. Thus, this includes performing wide studies of user responses to their searches, comparing their search results against those of other search engines, and conducting eye-tracking through a click- rate studies and constructing PR and other marketing campaigns.
How will SEO help businesses to Grow?
The recent survey says that the digital market and marketing through search engines is adequately grown as never compared. The basic marketing strategy is always helpful for many businesses to grow, but is it that enough or do they still need to spend more time on marketing strategy is the big question in many organizations, companies or businesses.
Here is the answer— you can generate good revenue primarily with the help of Search engines through paid advertising; though the majority of this revenue will come from pay-per-use or cost-per-click models, in which the advertisers pay only for users who click on their ads. As we know that the search engines’ success depends on the relevance of their search results, manipulations in search engine rankings result in non-relevant results, and these type of results are generally referred to as spam, and should be dealt very seriously. Each major search engine employs a team who focuses solely on the result or eliminating the spam from their search results; this is generally referred as “web spam” teams. However, this matters to SEO professionals as they use more tactics to promote the products or service, and they should not land the spam by the search engines, as this would carry more risk of incurring penalties for the websites they work on.
The Human Goals of Searching
When we need some sort of information, or to know something it all depends on upon your search. The basic goal of any human search is to obtain the information relevant to a specific set of keywords or phrases you enter into the search field; which is also known as a query. A searcher may invent the query as a question, but the majority of searches are performed by simply entering word combinations, and leaving the search engines to do their work of determining the “objective.” One of the most important essentials to build an SEO strategy for a website is developing a thorough understanding of your targeted audience, and how they use combined words and concepts to obtain information about the services or products you provide. Once you know how an average searcher or more specifically your target market utilizes query-based search engines, you can more efficiently reach or retain those users.
Search engine usage has increased over the years; however, the major principle of conducting a search remains largely unchanged. Let us understand the following steps most of the search engine consists:
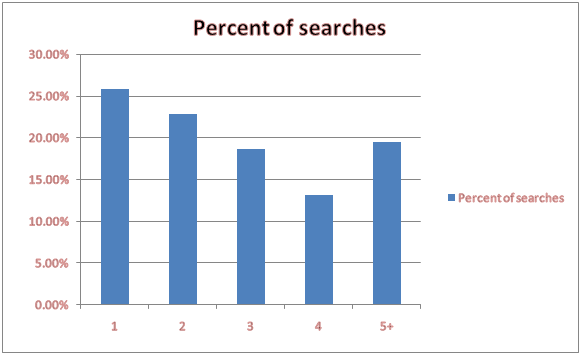
When this process results in the acceptable completion of a task, you can create a positive experience for the user by the search engine, and the site providing the information or the result.
We learn more on Digital Marketing strategies and how to determine Searchers Intent and the challenges for Search Marketers and Search Engines in our next blog.
...
Read More

The value proposition of Cloud computing — the delivery model for digitalization and innovation has evolved from cost reduction and scalability to mobility and cognitive computing. However, the other benefit is a path to improve customer loyalty using cognitive services through a cloud to create personalized promotions and interactive customer support.
This thinking has extended the idea of a cloud assessment beyond traditional and advanced IT analytics that aimed to improve the customer experience and expectations. The purpose of this customer-centric approach is not which cloud is the best fit for any application; instead, it should, which cloud is the most innovative in adding to hosting services.
The cloud suitability assessment in traditional approach is to evaluate the IT systems using prearranged criteria and to identify the best suitable cloud hosting environment. By implementing such environment you can evaluate cost reduction, agility, scalability, and flexibility. However, such assessments often result in creating a hybrid cloud (private and public) for enterprise-level customers.
While based on every organization’s IT need and policies, it is crucial to tailor assessment criteria which are typically included on latency (performance), accessibility, hardware dependency, data security/privacy and demand certainty. Thus, the end result is to migrate your application to the cloud, but that is not enough to be competitive in many markets today.
However, these assessments are like foundations to new analysis which aims to transform traditional IT systems into cloud-based systems to enhance the customer based services.
This new cloud assessment requires added evaluation criteria’s, such as cross-platform compatibility, integration involvedness, open technologies, and cognitive computing applicabilitys. These criteria’s can overlap with architectural design principles, and enable innovative services through IT systems running in the cloud.
Here are some questions that may help you to make out any gaps and achieve your innovative goals that go beyond legacy cloud migration.
This comprehensive assessment will make your systems or applications land in a cognitive ready cloud environment so you can speed up the design and implementation phase to innovative services.
The potential for these services is every time unlimited, so you need to consider the new insights made possible by cognitive computing. With the help of cognitive services process, you can see the tremendous amount of structured and unstructured data generated by billions of mobile devices every day.
It’s time to go beyond migrating your applications and systems into the cloud, and also look into its readiness for innovations how cloud and cognitive services could revolutionize your customer experiences. By doing so you could drive your digital transformation.
...
Read More